There is a dull hum permeating the industry of late – security is dead some say, others think it to be too costly to maintain, others still believe that what is needed is a change of perspective, perhaps a radical shift in how we approach the problem. What underlies all of these positions is a belief that the status quo is woefully ineffective and the industry is slated for self-destruction or, as a whole, we will succumb to a digital catastrophe that would have been avoided if only we had just…well, just done something different from whatever it is we are doing at the time something bad happens.
As we go round and round on the never ending hamster wheels provided as best practice guidelines and securty frameworks by security vendors, consultants, and pundits, we find ourselves trapped in an OODA loop that will forever deny us victory against malicious actors because we will never become faster, or more agile than our opponents. But to believe one can win, implies that there is an end that can be obtained, a victory that can be held high as a guiding light for all those trapped in eternal security darkness. We are as secure as we need to be at any given moment, until we are no longer so – when that happens, regardless of what you may believe, is outside of of our control.
One of the biggest trends in security over the past 5-6 years has been its movement into mainstream IT. Traditionally IT security has been seen as outside of normal business processes. Organizations tended to react driven by a security incident or compromise, an audit or compliance event, or due to perceived changes in the threat landscape. For the most part security has been and still is an afterthought.
There is little doubt that security lags innovation. For example the concept and delivery of cloud-computing was introduced and then it was realized that the lack of security – real and perceived – especially as it relates to visibility and control, was a huge inhibitor to adoption. The same is true for mobility; today many organizations are seeing their employees adopt shiny, new consumer computing devices, like the iPhone and iPad, and requesting access to corporate resources, yet most organizations are still struggling with managing and securing traditional computing assets, such as PCs and servers and there is limited enterprise-class support for these new devices.
For the most part security can only inform, rarely does it affect change, that job is left to the operational teams that must reconfigure a network device, harden a database, patch a workstation or disable services. Most security professionals lack an understanding of the operational environment that they work within and they lack the ability to modify that environment even if they did. So why do security professionals spend so little time understanding their role within an organization?
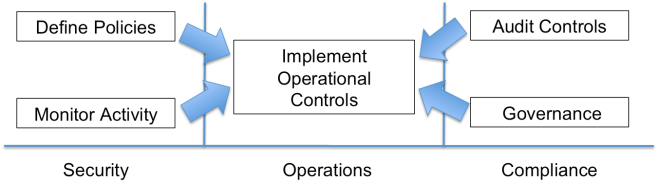
I would assert that the fundamental problem with security today is that it is not part of the operational lifecycle of IT and until we can integrate security into every elements lifecycle we will forever be left implementing security as an afterthought or bolting it on once we experience a compromise or undergo a TSA like groping of our networks from an auditor. Security must be operationalized, it must become part of the lifecycle of everything IT. This is the theme for 2011: Operationalizing Security.
- To experience wide-spread and main stream adoption security technologies must be operationalized
- To become operationalized security technologies must become integrated as a part of an elements lifecycle
- To become part of an elements operational lifecycle security technologies must provide output that is operationally actionable, integrated within the broader operational eco-system, and support current operational processes.

A-
Great stuff. I’ll add that IMHO data supports at least the positioning of InfoSec as a sort of “quality” mechanism for the IT lifecycle.
If you take Visible Ops for Security, the Verizon DBIR error rates and other evidence of at least an indicator, visibility and variance are huge risk reducers.
Obviously there is a “luck” factor, and a point at which there is very little ability to resist a determined, intelligent attacker – but for the most part significant breaches have a huge element of carelessness associated with them.
@Alex
You are absolutely correct we are our own worst enemy and most significant external attacks are a result of misconfigured, poorly administered and totaly ignored systems
I’ll put your call into my New Year wish list along with 2 other items:
1. A call for security architects to remember that Assurance is one of the foundational building blocks.
2. A VIPS (vendor intrusion prevention system) that filters out the silver bullet solutions, hyperbole on fog (sorry, I meant clouds), gross exaggerations and level one FUD from over stimulating c-level players.
@David
“VIPS (Vendor Intrusion Prevention System) that filters out silver bullet solutions, hyperbole on fog, gross exaggerations and level one FUD…”
yes that is awesome =)
“I would assert that the fundamental problem with security today is that it is not part of the operational lifecycle of IT”
All of the ISACA certifications are concerned with the integration of security with strategic and operational IT lifecycles.
You’re right.
Security as a stand alone process / department only exists because operations ‘does [it|IT] wrong’. As soon as operations starts ‘doing it right’, the current work of the precious security process / department will be an integral part of the daily organization.
Just like the man with the red flag we’d running in front cars, 100 years ago.
Pingback: Will Log Management Always Be an Afterthought? | Log Management Central
Why are we picking on cloud? What is wrong with cloud specifically, that hasn’t been pointed out by ENISA and can be offset with the right principles and controls, much like any system, app, or information/data asset grouping in an information security management program?
The US and European banks appear to be getting their acts together with the war against banking trojans. The author of ZeuS has recently retired.
eBay/PayPal and Facebook appear to be solving the challenges of web application security. STS and OAuth (and similar initiatives) are going to solve a swathing’s worth of problems that SSL/TLS and other authentication systems could not, as an example. This will extend from the web application world to the mobile app world.
Google and Amazon are really doing some neat behind-the-scenes stuff that will eventually catch on for cloud computing security. The challenges of secure multi-tenancy is largely dwarfed by the primary issue of managing Access/API keys for cloud SPI offerings, compounded by Cloudkick and other new ways of managing our clouds. Perhaps there will be a vulnerability management equivalent to Cloudkick’s network management — much like how Qualys has taken over the DMZ/LAN-based old school Enterprise vulnerability management.
Then there are the idiots who seek to destroy cloud for no reason, such as Microsoft and Apple. We’ll start to see your unidealistic view of innovation when mainstream desktops and device UIs are served via the cloud, and when they don’t have a Windows or Apple logo or run any apps, RDBMSes, or VMs made by Oracle or Adobe.
Our largest failure is reliance on browsers, e-mail clients, web/mobile apps, and the technologies that they are built on. If we can get rid of MySQL, Oracle 11g, .NET, Java, Flash, HTML5/Javascript, Acrobat Reader, Internet Explorer, Safari, Windows-Live/MacOSX Mail, Outlook, etc — then we will be on a path to something else, and that something else is likely to at least propose an architecture that is better suited to assurance and security principles.
However, we don’t need any technology to do this besides ones focused around usability for the things we want to protect and inability to build a market for the things we wish to defend against. Psychology and economics are still the dominant problems that will allow our adversaries to be continually ahead of us. Reduce code, reduce code growth, and reuse existing, assured apps. The open-source movement is great, but we need less projects and more consolidation. The same is true for the security industry and what some have referred to as “the new school infosec movement” — http://newschoolsecurity.com
Hey Andre,
Not sure what the “picking on cloud” comment is about, I don;t see anyone picking on cloud, there was simply a reference to cloud-computing as yet another technology innovation where security isn’t baked in and the result is people hesitant to adopt due to the real and perceived lack of security.
As to your other comment “If we can get rid of MySQL, Oracle 11g, .NET, Java, Flash, HTML5/Javascript, Acrobat Reader, Internet Explorer, Safari, Windows-Live/MacOSX Mail, Outlook, etc — then we will be on a path to something else…”
Yes that would be awesome, but that isn’t the reality we are all working in today, so it seems kind of pointless to discuss. Sort of like saying “If we could just get rid of the desire for folks to get high we wouldn’t have a drug problem”
Hi Amrit,
Good post, and I agree – security should be incorporated into everything IT.
However, I know this has been preached for a long time now in certain parts of IT (software development for example), but I can’t see that it has made any difference. I don’t know if it’s the heritage of old code (in terms of old bugs and holes), the complexity of developing secure code or simply the lack of a business perspective to it that we should blame for this, but the fact is that there are just as many bugs now as then – and they’re often more exposed thanks to our rapidly shrinking world.
I think we are facing the same problem with operationalizating security in the rest of IT; the complexity is so high and it only requires a single oversight to enable an attack. And let’s face it: Secuity is rarely a busniess enabler like we want it to be.
No certifications, life cycle integrations or fancy leading practices can change this fact. So we need to cooperate and develop methods for sharing security data across organizations to enable swift damage control and proactive measures. We also need to take a long, hard look in the mirror and figure out how security can revitalize itself to be a business enabler. That’s the only way to integrate security into every elements lifecycle of IT.
Sorry for a boring “yeah, you are TOTALLY right” comment 🙂
Yeah, you are TOTALLY right! From SIEM to PM to DLP to hell know what, people BUY but never OPERATIONALIZE.
So, why buying boxes at $$$ cost is SO much more popular than using them well as a part of a well-thought program (=operationalizing)?
We need a biometric ID (it could be incorporated into our drivers license or passport) that everyone in our society carries so that NO ONE can claim discrimination (leaving us open to many major lawsuits) and so that EVERYONE is held accountable as there are many people within our borders at this point who need to be held accountable. A boarder within our boarders so to speak.
It is very important for the ID to expire according to ones LEGAL status.
An expiration date that expires according to one’s legal status (citizen, worker, guest, student, legal status etc.) as opposed to a predetermined amount of time. This would ultimately make it possible for us to become a more welcoming society and to expand our guest worker program, student exchange program, etc. It would also allow us to hold in-country people accountable such as sex offenders. For example, the 9-11 terrorists were here legally, but their period for stay in this country had expired. Unfortunately, they were still able to function in our country. With this system it is highly unlikely that they would have been able to carry out the attack. When their time had expired, they would not have been able to continue to function in our country. For example, they would not have been able to take flight lessons, rent cars, rent hotel rooms, buy airline tickets, board a plane or enter into any designated/secured site, space, or location because they would have been expired. It’d be similar to trying to go through an EZ-pass when your card has expired. We have always had to look for the needle in the haystack. With a system like this the haystack disappears as one’s legal status expires exposing the needle. The system could also be effective in making sure that sex offenders, and others who have not met their legal obligations are held accountable.
Anything short of EVERYONE in the population participating in the system will only result in us looking for a needle in the haystack, if something happens. If everyone had been using a system like this on 9-11, chances are, it would not have occurred. This system will go a long way to getting issues of work visas, student visas, etc., under control, but will also have impact on how we deal with sex offenders, drug dealers, and credit card, check and bank fraud, etc.
We do not want to see our government putting together a commission or engage in a blame game to figure out why we didn’t take preventive action ahead of time. This is not a time to be politically afraid to do what is right for today’s world. We should ALL be proud to be part of the solution.
Catherine A. Haala
Crosscheck Identification System International
U.S. Patent No.: 6,934,861 B2
Pingback: 资讯科技及信息安全播客 » Blog Archive » Network Security Podcast, Episode 222
The great points Amrit Williams makes in “2011: The Death of Security As We Know IT or Operationalizing Security” made me think that IT security isn’t the only kind of security that needs major changes put into action as soon as possible. Indeed, Amrit’s persuasive points would appear to apply to US national security as well.
For instance, it appears US national security measures might be “driven by a security incident or compromise” with solutions that lag “innovation.” Is this the best way? Or, as with IT security, perhaps national security measures should be more proactive than reactive, and adopt an “operationalized” approach across the US, integrated into the daily life of everyone and “operationally actionable.”
I agree with Amrit’s assessment that integrating security into the entire lifecycle of all IT elements is an absolute necessity to have the best possible IT security. Similarly, regarding national security, my research has led me to believe there is an “operationally actionable” national security system that would enable us to have the best possible US national security, and it even has the ability to “affect change.” This national security system is called Crosscheck Identification Systems International (CISI) and it is U.S. Patent No.: 6,934,861 B2 by Catherine A. Haala.
CISI would “operationalize” national security by implementing a national biometric ID system – which can be incorporated into already existing items like a driver’s license or a passport – that could make the US and, in turn, the world safer while holding everyone accountable without discrimination.
The elements to make CISI effective are:
• An expiration date that expires according to one’s legal status (citizen, worker, guest, student, etc.) as opposed to a predetermined amount of time.
o CISI functions as a prerequisite to entering into any transaction or any secured site, space or location.
o When a person’s time expires, they would not be allowed to function in the US. For example, they would not be able to take flight lessons, rent cars, rent hotel rooms, buy airline tickets, board a plane or enter into any designated/secured site, space, or location.
o CISI could also be effective in making sure that non-reporting sex offenders and others who have not met their legal obligations are held accountable.
• Participation by all.
o In order for any ID system to be truly effective, EVERYONE in a population MUST participate in the system. We must all be willing to be a part of the solution.
o CISI does not discriminate, as everyone participates.
o With everyone participating, it will be more a compelling, easier and less expensive national security system to put into effect. An existing office such as those for Social Security, passports or driver’s licenses could be expanded to issue CISI’s biometric cards, with a branch available to do renewal reviews for students, workers etc.
• The card must be tamperproof and have biometric ID so that forgery is not an issue.
o Identity theft affects millions of people and is a major problem in today’s society. CISI will help pay for itself by preventing identity theft, credit card fraud, bank fraud and check fraud , drug dealing, illegal business
The main advantages of CISI include:
• Effective nationwide protection from terrorism, illegal activities.
• Non-discriminatory application due to mandatory participation by everyone in the population.
• Profiling unnecessary.
• Predetermined expiration based on an individual’s legal status (citizen, immigrant, tourist, student, guest-worker, etc.).
• Ensures accountability.
• Compatible with various government threat levels (Severe, High, Elevated, Guarded, or Low).
• Compatible with existing IDs – Driver’s License, Pilot’s License, Passport, Etc.
• Tamper/Fraud proof.
As with IT Security, it would appear that if reconfigure our mainstream national security system and adopt widespread, integrated change through CISI, we can “operationalize” all of the elements of the lifecycle of everything national security related, and help make the US – and the world – a much safer place.
And maybe, just maybe, thanks to Amrit Williams and Crosscheck Identification Systems International, this will be the theme for 2011: Operationalizing IT Security AND US National Security.
Great post as usual Amrit.
Over the years of this industry I have seen the constant battle between Security (the restriction of access, usually to a cumbersome level) and Access (to the point of intrusions and vulnerabilities), with access usually winning out for a number of reasons. We find ourselves in a corner with paint on nearly all sides due to the anonymity of the internet and the inability to define security measures early in the architectural process. Let’s be honest: Apple’s resurgence, namely in the meta-market of media access and delivery, would not be nearly as sexy if it was less accessible and more secure.
The typical response to this argument is why not both – and indeed while this is technically possible it is probably not feasible due to the motivations of the decision makers. This is not a problem that is isolated to IT security. For example, look at the difficulty in defining an illegal alien and their access to national resources. While, technically, this should be an easy definition there are numerous other motives at work and thus the boundaries become difficult to define. Ergo – how do you implement a policy if you cannot accurately agree on how to define your players?
In the IT world, this problem is only going to get worse. The Cloud is a fantastic idea from an access perspective, however to the CIO/CSO this is nearly a complete dismantling of border security. This is not to imply that the Cloud concept is insecure by nature, but rather that it places more emphasis on trust than many CISOs will be comfortable with. Think of the impact that the several Choice Point breaches have had and now project that at the storage and access parts of a company’s infrastructure.
How does one define friend/foe in such an infrastructure, let alone define policies that actually work for both sides of the equation?
The problem may not be completely solvable until a system of increased personal accountability and identification can be instated. The current WikiLeaks scandal is evidence enough that a single failure, combined with a single point of failure, is disastrous. Being able to correctly identify who you are and what you are able to access personally and professionally in an infrastructure with blurred lines is critical. However, that will bring up civil liberties concerns much in the way the Patriot Act has – and probably be received with the same sort of scorn.
I believe that the job of a Security Professional will be plentiful and secure (pun intended) for a long time, however the battle lines will become very different as we move forward in these new and exiting technologies.
Excellent post – and great point Amrit.
Couldn’t agree more — and it reminds me of some Soto Zen masters that maintain that the purpose of sitting zazen isn’t to achieve enlightenment; sitting zazen is itself enlightenment, and it’s something you do every day. We’re never going to be secured, but we can strive to do things securely every day.
Pingback: Must read!! The single best security blo… « Jae Ho's Weblog
Awareness of prevalent threats is crucial to develop more secured products
Launch of a new Conference Series
A new conference series has been launched. TakeDownCon (TDC) will bring together information security researchers and technical experts, both the brightest and darkest, from the corporate and government sectors to academic as well the underground, and make it into one of the world’s premier infosec event where the latest security threats are presented and debated, and vulnerabilities are disclosed and scrutinized. NOTE: TDC is highly technical, and only presentations that encompasses technical demonstrations will be accepted.
Why TDC?
– Concentrates on Attack and Defense, from a technical perspective.
– Only technical presentations will be featured
– No policies and management issues will be discussed. Its about hacks, cracks et all.
– Relaxed and casual setting. No frills. No luxuries. Thus making it comfortable for all attendees.
-Highly technical THROUHGOUT the event. TDC targets ONLY the technical experts, engineers, researchers (aka hackers)
– Affordable. We designed TDC to be accessible to the masses. Knowledge acquisition should not be hindered by financial restraints. So we will be expecting a big crowd.
– There are also multiple training classes available pre-event.
TakeDownCon will make its debut in Dallas, TX from May 14 – 19, 2011.
The call for paper is open now. To submit a paper to be presented, please visit http://www.takedowncon.com/cfp
Pingback: Security Blogger Meetup 2011 : “Security Thought Leaders” in the Spirit of Chris Eng - Microsoft Security Blog - Site Home - TechNet Blogs
Pingback: Security Week in Review: February 18, 2011 - Microsoft Security Blog - Site Home - TechNet Blogs
Security really lags innovation. Since there is this HUGE need to innovate, security also falls back. They are inversely proportional.
Excellent site, blog and interesting post, keep up the good work 🙂
Me han encantado la mayoría de los comentarios.
Gracias.
Pingback: Keen to explore the Infosec Blogosphere? Here’s a useful map (Thanks to #RSAC) « Countdown2infosecurity’s Blog
Nice Information Shared….Keep it up.