We all know that IT security and operations is becoming a more challenging and untenable problem day by day – see “Top 10 Reasons Your Security Program Sucks and Why You Can’t Do Anything About it” – The reality is that we continue to build on top of inherently insecure and fundamentally weak foundations, such as the operating systems and routing infrastructures that power much of the global economy.
We need an alternative to the current computing paradigms that all organizations struggle with.
It is under pressure…
- Increasingly hostile and sophisticated threat environment
- Regulatory compliance pressures
- Evolving business and technology demands
- Supporting complex and distributed computing environments
- Decreasing IT budgets
The operating system is the root of all evil…
- Environments are becoming more complex, more distributed and increasingly overwhelmed with security threats and regulatory compliance pressures
- IT has more tools deployed then ever in history creating a massive management burden
- All security and management technologies rely on the integrity of the operating system
- The majority of operating systems are inherently insecure
- Operational failures and compromise render traditional tools useless
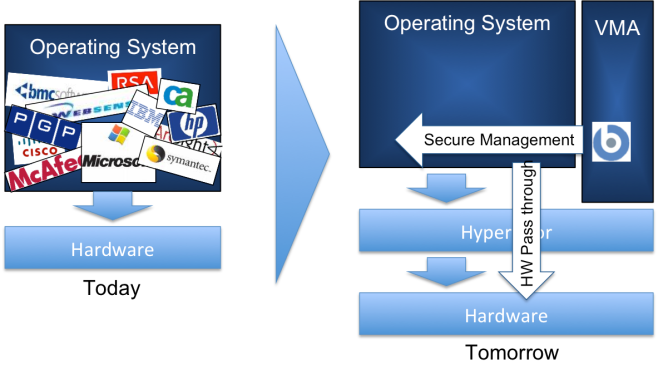
Figure #1: the total suck that is systems and security tools running within the context of the OS
Security and systems management must be abstracted from the context of the operating system…
- Virtual Management Agent (VMA) is a locked-down secure environment isolated from the operating system
- VMA is not impacted by the compromise or operational failure of the guest operating system
- VMA provides out of band management independent of operational state of the OS
- VMA has full visibility and control over operating system and tools running within the OS context
- VMA can quickly re-image, lock, pause, or change the state and context of the guest images (OS)
- VMA has visibility and control over ingress/egress traffic to/from the guest images (OS)
Figure #2: The path to enlightened systems and security management of end user computing devices
It looks simple on paper, but there are many issues with management, isolation, dealing with distributed computing environments, and of course the details of PC vs Server hypervisors, etc…all of which we will address in the coming days with a series of post on how to own the OS.
The Bottom line: the current state of Information security is a never ending game of continuously reacting and responding to new threats, operational failures, and crappy products. The ability to abstract security and systems management away from the operating system will revolutionize the method and efficiencies of IT management.


The Windows OS which because Microsoft owns the biggest market share is the most vulnerable OS on the market. Linux, FreeBSD, Solaris, and OpenBSD are more resilient operating systems. If you want to hack them, you look for flaws in the applications running on them because the operating systems themselves are pretty solid. Sandboxing the problem by using a virtual machine solution might save a few bucks in administrative and security costs, but it’s like putting a firewall between a vulnerable system and the Internet – it’s a patch for fixing a software problem. If we want a safer computing experience, then software makers will have to have some skin in the game and accept some liability for writing crappy products. This is Schneier’s proposal. There really is no alternative unless you decide to buy in to Microsoft’s argument that a tax should be levied on all Internet users to quarantine and clean infected systems of malware which is nonsense.
Hey jbmoore,
Thanks for the comments. Couple of observations:
– The *nix variants you mention can be just as vulnerable and insecure as Windows. It really is in how one configures, administers and implements technical controls in the operational environment that increases or decreases the attack surface and the ability to return to homeostasis when a compromise does occur. Additionally there are tons of vulnerabilities and exploits that take advantage of various low-level aspects of *nix operating systems, including the IP stack – so it really isn’t true to say they are more resilient or more secure
– Operating systems (almost all of them) and the routing infrastructure they use for communications are inherently insecure. The reality is that there is no way to eliminate all security threats. The best we can do is to limit the probability of a successful compromise and when one does occur, which it will, to limit the impact on the operating environment.
Client HV’s enable 2 very significant improvements over the current situation
1. Current tool sets for maintaining the health and security of computing devices are isolated and no longer reliant on the integrity of the operating system – this could significantly limit the ability for malware or malicous actors to bypass operational controls
2. If the OS is compromised or experiences an operational failure you can return to a golden image literally within seconds
I don’t think we can effectively legislate ourselves into more secure software – not only does it contradict the entire concept of free market capitalism, it would most result in significantly more expensive software costs and at the end of the day we would still have security issues.
Yes the MSFT tax is nonsense – but then so was Bill Gates comment in the early 2000’s when he said that Microsoft would fix all the security problems within the next 3 years 😉
I don’t entirely agree with your first point, but your second point is valid and true. Operating systems are all becoming more robust and resilient. Therefore, attackers are switching to compromising applications running on the these systems to gain access and then leveraging that access to gain further system privileges. Witness the Google Aurora attacks. The attackers chose the victims, the OS, and the applications they were going to exploit in very targeted spear phishing attacks. Changing either the OS or application used for the exploits may have made the attacks fail, but Windows and Adobe products were targeted because the attacker had a higher chance of success to gain access to Google’s internal network. There were other mistakes made such as running Perforce SCM software on Windows systems under the system account and not enforcing more stringent security on their SCM servers. Software exploitation attacks should be seen as akin to aircraft accidents, a chain of events leading up to a bad conclusion which could have been prevented or mitigated if one of the links in the chain had been done or practiced differently.
While no software is perfect, Unix and its clones are more robust. I suggest you try an experiment. Ask Core Technology for a demo version of Core Impact or Immunity Inc. for a demo of Canvas and run them against the latest versions of FreeBSD, Linux, Solaris, and Windows. The results will be surprising and you’ll have much less success compromising Unix and its variants.
A VM or sandbox will be only a stop gap measure, and the convenience of such an approach should be weighed against the risks involved in using it. It is just a variation of reimaging a real system but you are replacing a compromised vm file with a clean vm file or snapshot. So, it is more for convenience than security because you are minimizing the time and cost of rebuilding the compromised system by using a vm solution instead of a real computer. (You haven’t solved your security problem. You’ve just made it easier to recover from security lapses or errors.) You may be increasing your risks for this convenience if the attacker can compromise one guest and then compromise other guests or the host via the covert communication channels that exist between the virtual and host systems. After all, the virtual machine software is just another application to be exploited. If they can break into the hypervisor, then they can hide so effectively that you may never detect that you’ve been compromised. I enjoy the virtual technology you espouse and use it almost daily, but in the end this looks like convenience masquerading as a security fix.
The inherent weakness of capitalism is the erosion of ethics and standards. If your competitor writes crappy code with a prettier GUI and beats you to market, he makes more money while his customers may suffer since his EULA protects him from being sued for his customers’ losses. You have no choice if you wish to compete with him but to cut corners and race to the bottom. Therefore, you have a Gresham’s dynamic in play where the bad practices of your competitors forces you to play their rigged game if there is no outside authority to stop the cheating. Bad practices drive good practices from the market. We’ve seen this happen with the banking system. We’ve seen this in ratings agencies marking trash products as AAA investment grade. We’ve seen it in China where milk producers substituted chalk and melamine for real milk. Why should the software business be any different from any other business and immune to some sort of government standards to protect a whole society from losses and bad industry wide practices? Self regulation does not work and totally free markets do not work because at some point they will fail because of an erosion of trust or other problem caused by a Gresham’s Law dynamic arising. If businesses are held liable for their bad actions, then Gresham’s dynamics do not arise because incentives to cheat and skimp on quality are penalized.
Links:
http://www.coresecurity.com/
http://www.immunityinc.com/products-documentation.shtml
Click to access Stealing_Guests_The_VMware_Way-ShmooCon2010.pdf
http://en.wikipedia.org/wiki/William_K._Black
http://en.wikipedia.org/wiki/Gresham's_law
Hey Amrit,
All anyone ever does is complain about how bad security is, how stupid everyone is, etc etc etc. So I really appreciate you taking a fresh approach to the problem and suggesting an alternative. What can companies like Triumfant do to be a part of this revolutionary phase of security?
Warm Regards,
Mitch Quinn
Pingback: Meet the new desktop… not the same as the old desktop « The Neocleus Blog
There is no doubt that hosted virtual desktop are hot. And organizations are using HVDs to keep infrastructure costs low, increase internal management control of its IT systems, and support productivity from anywhere.
Also, Microsoft recently released a Case-Study of an Asset Management Firm Uses Hosted Desktop Solution to Reduce IT Budget by 50 Percent. And the benefits are not only limited to Cost savings, but customers also recorded an increased workforce productivity, enhanced IT control, and greater operational flexibility.
Read this case-study:
http://www.microsoft.com/casestudies/Case_Study_Detail.aspx?CaseStudyID=710000001352